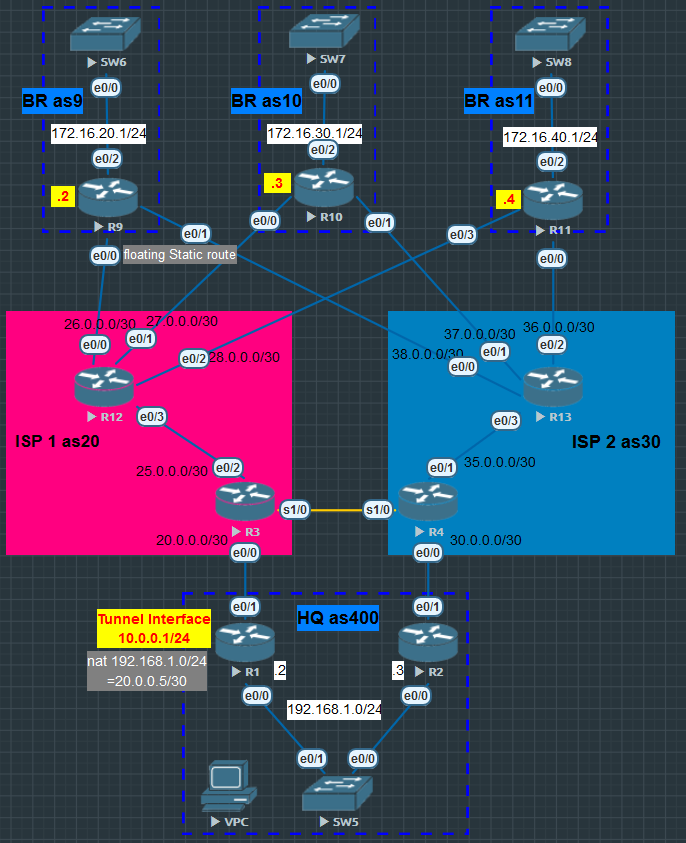
Vpn Multipoint Sample Configuration
#R1 (HUB Router)
#Phase 1
crypto isakmp policy 100
hash md5
authentication pre-share
group 1
encryption aes
lifetime 86400
!
exit
!
crypto isakmp key 6 KEY address 26.0.0.2
crypto isakmp key 6 KEY address 27.0.0.2
crypto isakmp key 6 KEY address 28.0.0.2
#Phase 2
crypto ipsec transform-set TRANSET esp-aes esp-sha-hmac
mode transport
exit
!
crypto ipsec profile PROFILE
set transform-set TRANSET
set security-association lifetime days 1
#Create a Tunnel
#Note: Tunnel interface default bandwidth is 100
#Set MTU to 1400 to avoid payload fragmentation
#Set tcp adjust-mss to 1360
Int tunnel 100
Ip add 10.0.0.1 255.255.255.0
!
bandwidth 100000
ip mtu 1400 #Adjust MTU size
ip tcp adjust-mss 1360 #Adjust tcp-adjust-mss size
!
!
!
tunnel source 20.0.0.2 or e0/1
tunnel mode gre multipoint #Tunnel mode is Multi-point
tunnel protection ipsec profile PROFILE
!
ip nhrp network-id 100 #enable NHRP in this tunnel interface
ip nhrp authentication NHRP
ip nhrp map multicast dynamic
!
no ip next-hop-self eigrp 100 #We will use EIGRP for the tunnel peering
no ip split-horizon eigrp 100
R9 (spoke routers)
Phase 1
crypto isakmp policy 100
hash md5
authentication pre-share
group 1
encryption aes
lifetime 86400
!
exit
!
crypto isakmp key 6 KEY address 20.0.0.2
Phase 2
crypto ipsec transform-set TRANSET esp-aes esp-sha-hmac
mode transport
exit
!
crypto ipsec profile PROFILE
set transform-set TRANSET
set security-association lifetime days 1
Create a Tunnel
int tunnel 100
ip add 10.0.0.2 255.255.255.0
!
bandwidth 100000
ip mtu 1400
ip tcp adjust-mss 1360
!
tunnel source 26.0.0.2
tunnel mode gre multipoint
tunnel protection ipsec profile PROFILE
!
ip nhrp network-id 100
ip nhrp authentication NHRP
ip nhrp map multicast 20.0.0.2 (“Public IP add of HUB Router”)
ip nhrp map 10.0.0.1 20.0.0.2 (“Private IP of HUB Router / Public IP add of HUB Router”)
ip nhrp nhs 10.0.0.1 (“Private IP add of HUB router / Tunnel int”)
!
!mirror this config on R10 and R11
!
!done…
Verify:
Show dmvpn
Sh ip nhrp